We live in a century where pretty much everything is technology based. Most people have at least one type of technology in his or her house if not more. The main type of technology that people have is a computer. Computers are very helpful but if it doesn’t have a good network security then the information that is in the computer could be easily hacked and stolen. The easiest way to protect this is by knowing how to defend network attacks.
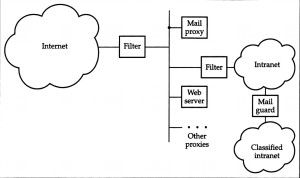
The method of network defense that is most widely used is a firewall. A firewall is a barrier between the local network and the Internet that filters out anything that could be considered harmful. There are three types of firewalls: one that filters at the IP packet level, at the transmission control protocol session level, or at the application level.
The first type of filter is basic packet filtering, which filters packet addresses and port numbers. This type of filtering can block any type of IP spoofing attack that comes near the firewall of the computer. It ensures that no packet that is coming from or around the local network is allowed to enter and pass through the firewall. It can also stop any malformed service attacks that are sent to the host that tries to persuade the host that it is safe to connect to. One of the easiest ways to defeat an incoming attack at this level is to fragment the packet in a way that initial fragment is overwritten by a succeeding fragment, which replaces an address with one that violates the firewall’s security.
The second type of filter is a more complex one called circuit gateways. This type of filter reassembles and examines all of the packets in each TCP circuit. This is more expensive than basic packet filtering because in this firewall you can add a virtual private network over the Internet by doing encryption from firewall to firewall and screening out websites. The only problem with this kind of firewall is that circuit gateways cannot prevent any attacks at the application level, which is mainly composed of malicious code.
The third and last type of firewall is the application relay. This type of firewall acts as a proxy for one or more Internet services such as mail and web. This is the level of protection where you can enforce rules such as stripping out macros from incoming word documents, and removing active content from web and mail pages. This firewall is the one that provides a comprehensive amount of protection against a wide range of threats. The problem with this type of firewall is that it interferes with the run of latest applications that the user wants to run.
Firewalls can only do a small number of things but it is possible to make them simple and remove any components from the underlying operation system. The best kind of firewall is the one that has the best configurations because if there is too much to do for the firewall then it wont be effective.
Source: http://www.cl.cam.ac.uk/~rja14/Papers/SE-18.pdf